Written by John Remsey, IMEC Senior Technical Specialist
Cybersecurity has become a hot topic within manufacturing over the past months, especially for the Defense supply chain with the federal government increasing their emphasis on addressing threats to the security of information. In December 2015, the U.S. Department of Defense (DOD) released a rule to the Defense Acquisition Federal Regulation Supplement (DAFRS) that requires government contractors to implement the requirements of National Institutes of Standards and Technology (NIST) Special Publication (SP) 800-171 by December 31, 2017. With this deadline fast approaching, conversation, and urgency, to become compliant is increasing.
The requirements of NIST SP 800-171 are intended to protect the confidentiality of Controlled Unclassified Information (CUI) in non-federal organizations and their supply chains. A failure to meet these requirements may result in the loss of supply contracts and liability for the organization should an escape of CUI occur internally or their suppliers and service providers. While organization doing business with the federal government should expect these types of requirements to increase over time, it is good practice for all organizations (manufacturers included) to protect information they have been provided during business activities.
While Cybersecurity, and the external threats commonly associated with it such as Hacking, Spyware, Ransomware and Malware, is very important, it’s also important to realize that it is just ONE PIECE of an effective Information Security Program. An organization’s exposure to information vulnerabilities extends well beyond the interconnected world. A comprehensive Information Security program also includes: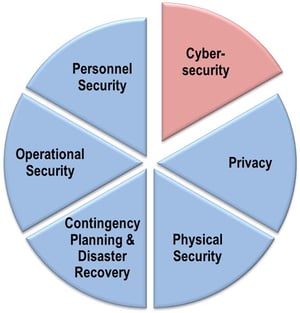
• Privacy: Adequately protecting the information and identity of your Employees, Customers, Suppliers and other Resource Providers. Ensuring that controls, systems and procedures are in place to restrict access to this information to only those who absolutely need it and include procedures for the archiving and purging of excess, expired or unnecessary information.
• Physical Security: Protecting, limiting and monitoring access to information stores and access points. Securing data storage, access points and other means of physical access.
• Contingency Planning & Disaster Recovery: Developing, testing and deploying the tools and processes needed to quickly and effectively recover information in event of a catastrophe. Speed to recovery from an information event can be the difference between recovery and loss of operations.
• Operational Security: Protecting private business intentions, processes and Media response channels. Limiting the access to strategic and market differentiating information. Developing an informational response plan to quickly and effectively address any potentially adverse information regarding the organization.
• Personnel Security: Implementing background checks for staff and service providers with access to information as well as behavior monitoring to proactively detect exposure risks. Implement the tools and procedure necessary to have confidence that those invited to access information are focused on using it for the good of the organization and its stakeholders. Monitor activity at all levels and implement triggers and warnings should information flow or user behaviors vary beyond normal expectations.
Manufacturers have a variety of tools available to help pursue comprehensive organizational security, starting with cybersecurity. The first step is to determine one’s existing cybersecurity protections and tools and identify easy gaps to fill. Taking protective steps can decrease the time and resources spent on a security breach. Contact IMEC at info@imec.org or 888.806.4632 to learn more about existing self-assessments to get your company started.




